Secrets
Secrets store sensitive data like passwords, tokens, or keys. They may contain one or more key value pairs.
This page is about secrets in general. For details on setting up a private registry, refer to the section on registries.
When configuring a workload, you are able to choose which secrets to include. Like config maps, secrets can be referenced by workloads as either an environment variable or a volume mount.
Mounted secrets are updated automatically unless they are mounted as subpath volumes. For details on how updated secrets are propagated, refer to the Kubernetes documentation.
Creating Secrets in Namespaces
In the upper left corner, click ☰ > Cluster Management.
Go to the cluster where you want to add a secret and click Explore.
To navigate to secrets, you may click either Storage > Secrets or More Resources > Core > Secrets.
Select the Namespaced tab.
Click Create.
Select the type of secret you want to create.
Select a Namespace for the secret.
Enter a Name for the secret.
noteKubernetes classifies secrets, certificates, and registries all as secrets, and no two secrets in a namespace can have duplicate names. Therefore, to prevent conflicts, your secret must have a unique name among all secrets within your workspace.
From Data, click Add to add a key-value pair. Add as many values as you need.
tipYou can add multiple key value pairs to the secret by copying and pasting.
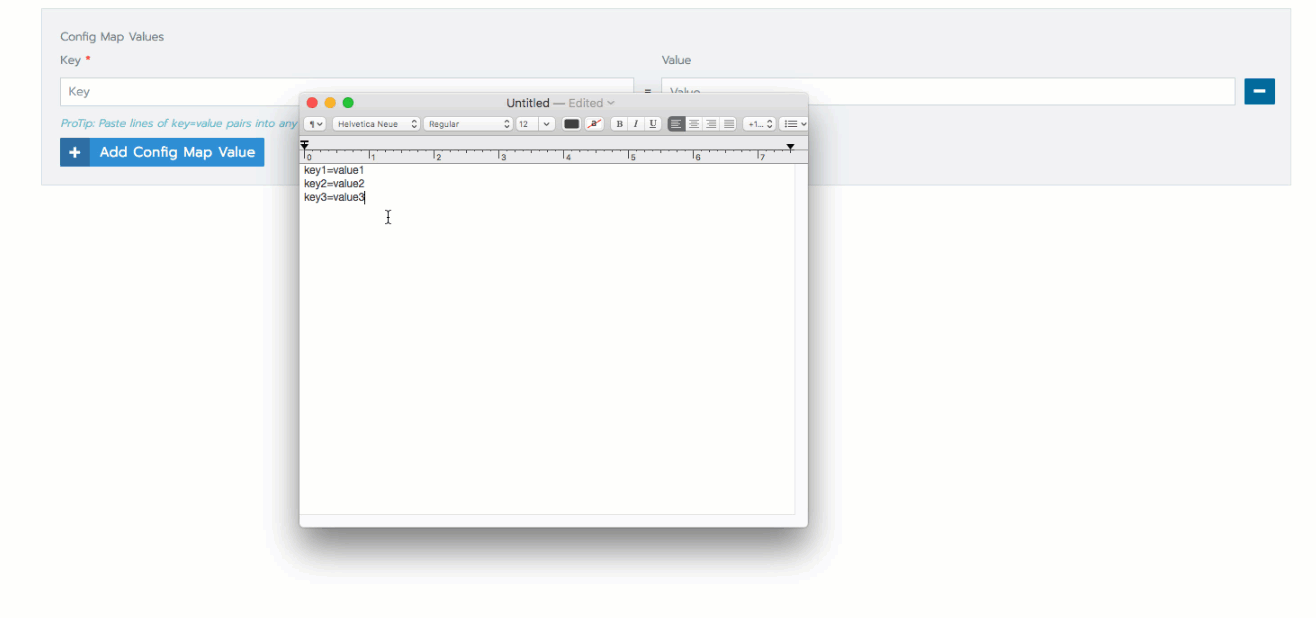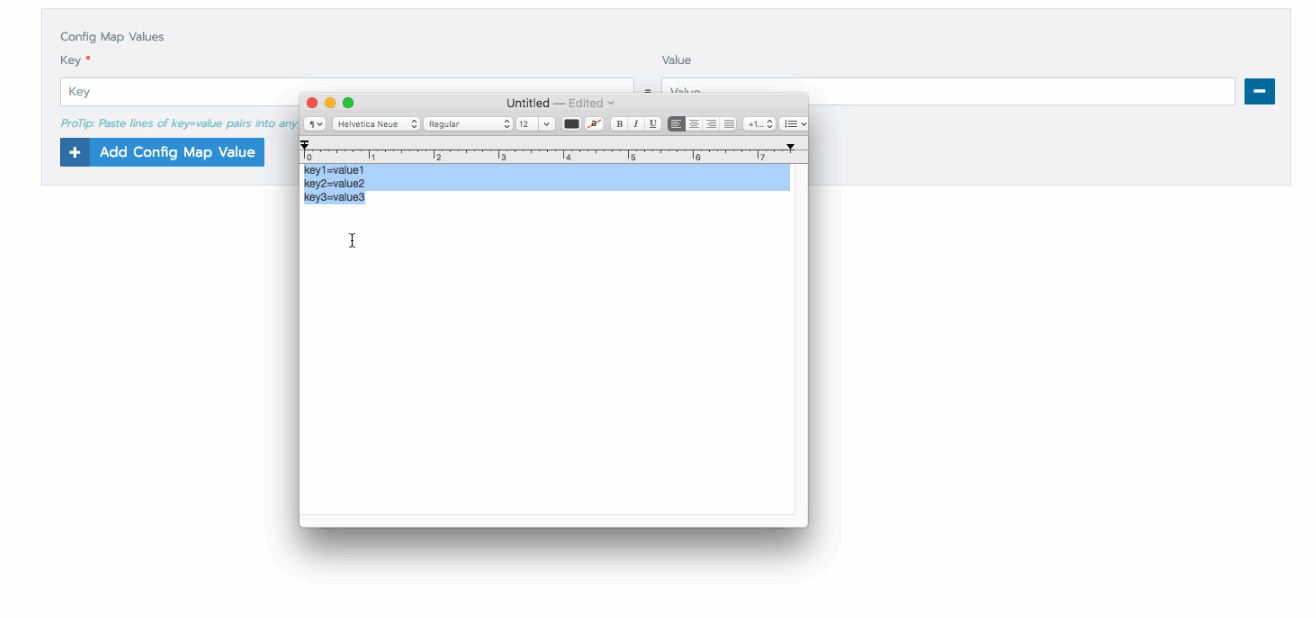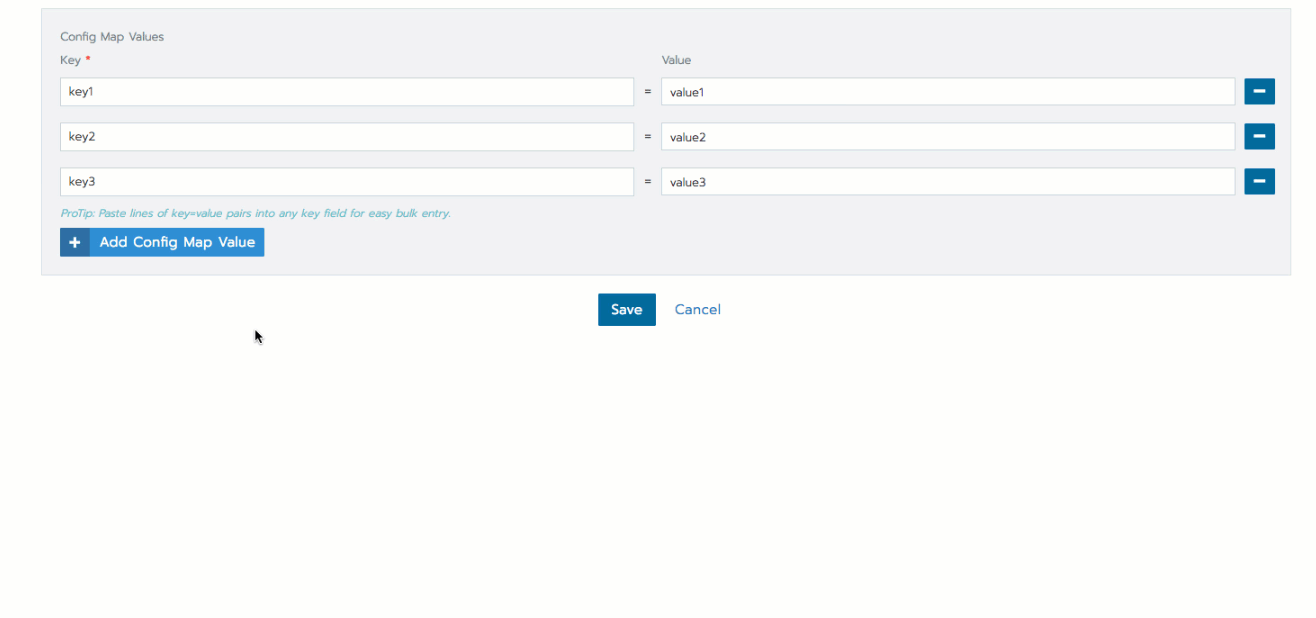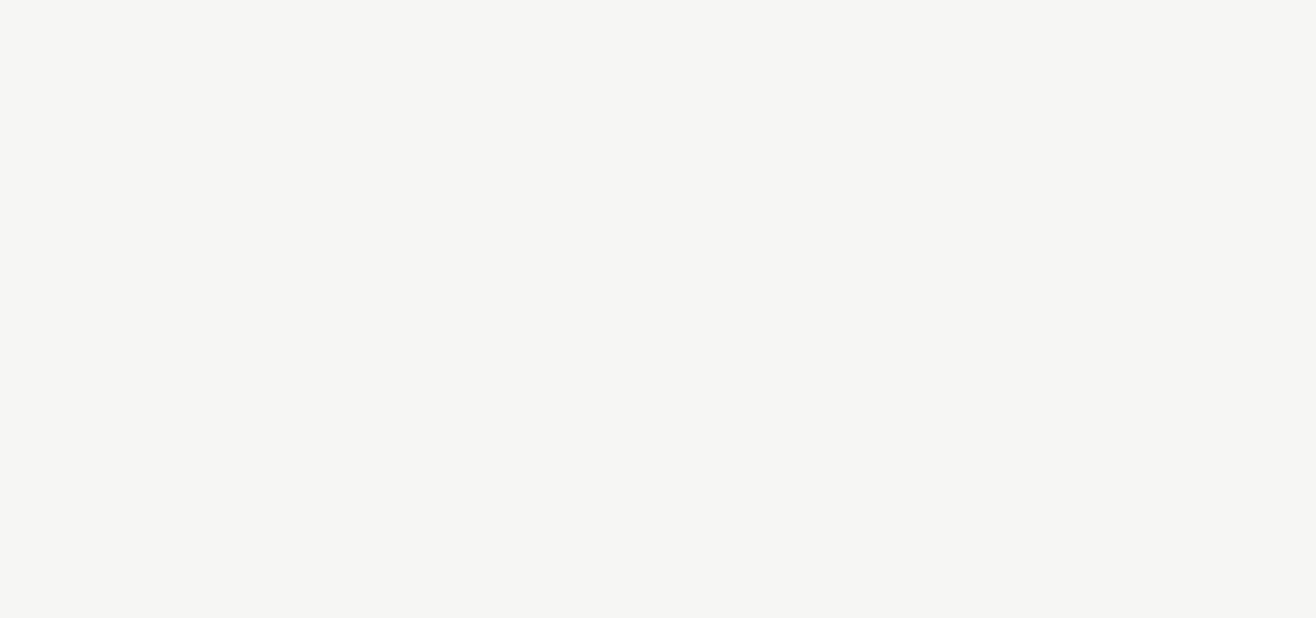
Click Save.
Result: Your secret is added to the namespace you chose. You can view the secret in the Rancher UI by clicking either Storage > Secrets or More Resources > Core > Secrets.
Mounted secrets are updated automatically unless they are mounted as subpath volumes. For details on how updated secrets are propagated, refer to the Kubernetes documentation.
Creating Secrets in Projects
When creating a secret in a project scope, the secret is copied into all namespaces within the project.
Creating a Project Scoped Secret in the UI
In the upper left corner, click ☰ > Cluster Management.
Go to the cluster where you want to add a secret and click Explore.
To navigate to secrets, you may click either Storage > Secrets or More Resources > Core > Secrets.
Select the Project Scoped tab.
Click Create Project Scoped Secret.
Select the type of secret you want to create.
Select a Project for the secret.
Enter a Name for the secret.
noteKubernetes classifies secrets, certificates, and registries all as secrets, and no two secrets in a namespace can have duplicate names. If you create a project scoped secret that has the same name as an existing secret in one of the project namespaces, the existing secret is overwritten.
From Data, click Add to add a key-value pair. Add as many values as you need.
tipYou can add multiple key-value pairs to the secret by copying and pasting.

Click Save.
Result: Your secret is added to each namespace within the project. You can view the secret in the Rancher UI by clicking either Storage > Secrets or More Resources > Core > Secrets.
Creating a Project Scoped Secret with kubectl
Project scoped secrets work by creating the original secret on the management cluster in what's known as the "Project Backing Namespace". Rancher stores important project related information in this namespace. You can find it in the status.backingNamespace field in the project CRD, or by doing kubectl get projects -A in the management cluster.
In order for the secret to be acknowledged by Rancher as a project scoped secret, it also needs the label management.cattle.io/project-scoped-secret: <projectID>.
Example yaml:
apiVersion: v1
data:
key: ZG9n
kind: Secret
metadata:
labels:
management.cattle.io/project-scoped-secret: p-vwxyz
name: test-secret
namespace: c-abc123-p-vwxyz
type: Opaque
In the above YAML, the namespace is the backing namespace of project p-vwxyz and the project scoped secret label references the projectID. When applied to the management cluster, all namespaces within the project p-vwxyz contain a copy of test-secret.
What's Next?
Now that you have a secret added to a namespace, you can add it to a workload that you deploy.
For more information on adding secret to a workload, see Deploying Workloads.